Introduction
Operational Technology (OT) is the backbone of industries like manufacturing, energy, utilities, and transportation, enabling the control and monitoring of physical devices, processes, and systems. With the increasing interconnection of OT and IT networks, OT environments are becoming more susceptible to cyber threats, highlighting the critical need for robust endpoint security. This article delves into the essence of OT endpoint security, its challenges, and strategies for implementing a resilient security framework.
Definition
Operational Technology (OT) Endpoint Security refers to the measures and solutions designed to protect the endpoints within operational technology environments, such as industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, and other critical infrastructure devices. These endpoints, including sensors, controllers, and HMIs (human-machine interfaces), are safeguarded against cyber threats, unauthorized access, and malware to ensure the integrity, availability, and safety of industrial processes. OT endpoint security focuses on minimizing vulnerabilities while enabling secure communication and functionality in environments where reliability is paramount.
What is OT Endpoint Security?
OT endpoint security refers to the measures and technologies designed to protect devices and systems within an OT environment from cyber threats. Unlike traditional IT environments, OT endpoints include industrial control systems (ICS), programmable logic controllers (PLCs), human-machine interfaces (HMIs), sensors, and other devices that directly interact with physical processes. The primary focus of OT endpoint security is to ensure operational continuity, safety, and reliability by preventing unauthorized access, malware attacks, and other vulnerabilities.
The Growing Importance of OT Endpoint Security
As industries embrace digital transformation and adopt Industrial Internet of Things (IIoT) technologies, the convergence of IT and OT networks introduces new vulnerabilities. Cyberattacks targeting OT systems can have devastating consequences, including:
- Operational Disruptions: A breach can halt production lines, disrupt energy supplies, or compromise transportation systems.
- Safety Risks: Cyberattacks on OT systems can lead to equipment malfunctions, endangering workers and the public.
- Economic Losses: Downtime and recovery costs from an OT attack can run into millions of dollars.
- Reputational Damage: A successful cyberattack can erode trust in an organization’s ability to secure its operations.
Challenges in Securing OT Endpoints
OT environments have unique characteristics that pose challenges to endpoint security:
- Legacy Systems: Many OT systems are decades old and lack built-in security features, making them vulnerable to modern threats.
- Operational Constraints: Unlike IT systems, OT systems often operate continuously and cannot be easily taken offline for updates or maintenance.
- Limited Visibility: OT environments often lack centralized monitoring, making it difficult to detect and respond to threats in real time.
- Diverse Ecosystems: OT environments comprise a mix of proprietary protocols and devices from various vendors, complicating standardization and security measures.
- Human Factors: Lack of cybersecurity awareness among OT personnel can lead to inadvertent vulnerabilities.
Key Components of OT Endpoint Security
To secure OT endpoints effectively, a comprehensive strategy should include the following components:
Asset Discovery and Management:
- Why It Matters: Organizations cannot protect what they cannot see. An accurate inventory of all OT assets is the foundation of endpoint security.
- Best Practices: Implement tools that provide real-time visibility into all connected devices, their configurations, and their security status.
Network Segmentation:
- Why It Matters: Segmentation limits the lateral movement of threats within an OT environment.
- Best Practices: Divide OT networks into zones based on risk levels and enforce strict access controls between zones.
Endpoint Hardening:
- Why It Matters: Hardened endpoints are less susceptible to exploitation.
- Best Practices: Disable unnecessary services and ports, apply patches and updates where possible, and use secure configurations.
Access Control:
- Why It Matters: Restricting access to OT systems minimizes the risk of insider threats and unauthorized activities.
- Best Practices: Implement role-based access controls (RBAC), multi-factor authentication (MFA), and least privilege principles.
Intrusion Detection and Prevention:
- Why It Matters: Detecting and stopping malicious activities early can prevent significant damage.
- Best Practices: Deploy intrusion detection systems (IDS) and intrusion prevention systems (IPS) tailored for OT environments.
Incident Response Planning:
- Why It Matters: A well-prepared response plan minimizes downtime and recovery costs in case of a breach.
- Best Practices: Develop and regularly test incident response plans, including OT-specific scenarios.
Emerging Technologies in OT Endpoint Security
1. Artificial Intelligence and Machine Learning (AI/ML):
AI/ML algorithms can analyze large volumes of OT data to identify anomalies and predict potential threats, enabling proactive security measures.
2. Behavioral Analytics:
Behavioral analytics tools monitor device and user behaviors to detect deviations from normal patterns, providing early warning of potential breaches.
3. Zero Trust Architecture:
Adopting a Zero Trust approach ensures that no device or user is trusted by default, enhancing security across interconnected OT and IT environments.
4. Secure Remote Access Solutions:
With the rise of remote monitoring and maintenance, secure remote access solutions ensure that external connections do not compromise OT security.
Best Practices for Implementing OT Endpoint Security
Conduct Risk Assessments: Identify critical assets, potential threats, and vulnerabilities to prioritize security measures.
Collaborate Across Teams: Foster collaboration between IT and OT teams to address security challenges holistically.
Invest in Training: Educate OT personnel on cybersecurity best practices and the importance of endpoint security.
Regular Audits and Testing: Perform routine security assessments, penetration testing, and audits to identify and address gaps.
Leverage Industry Standards: Align security measures with standards like ISA/IEC 62443 and NIST Cybersecurity Framework.
Case Studies: Lessons from OT Security Incidents
Stuxnet:
- Incident: A sophisticated worm targeted PLCs in nuclear facilities, causing physical damage.
- Lesson: The importance of robust network segmentation and regular monitoring cannot be overstated.
Triton Malware:
- Incident: Malware targeted safety instrumented systems (SIS) in an industrial facility.
- Lesson: Endpoint hardening and continuous monitoring are critical to protecting safety-critical systems.
Colonial Pipeline Attack:
- Incident: A ransomware attack disrupted fuel supplies across the U.S.
- Lesson: Securing remote access and having a robust incident response plan are crucial.
Trends in OT Endpoint Security
Zero Trust Architecture (ZTA):
Organizations are increasingly adopting Zero Trust principles, where no device or user is inherently trusted. This approach ensures continuous verification of endpoint security and reduces the attack surface within OT environments.
Convergence of IT and OT Security:
Integrated strategies that unify IT and OT security frameworks are becoming a standard. Advanced monitoring and incident response tools are being developed to detect threats across both environments, ensuring seamless protection.
AI and Machine Learning in Threat Detection:
AI-driven solutions are being deployed to enhance anomaly detection and threat intelligence. Machine learning models analyze patterns across OT endpoints to predict and mitigate risks proactively.
Endpoint Detection and Response (EDR):
EDR tools tailored for OT environments are gaining traction. These solutions provide real-time monitoring, rapid incident response, and comprehensive visibility into endpoint activities.
Secure Access Service Edge (SASE):
SASE frameworks are being implemented to ensure secure and optimized access to OT systems. By integrating security functions with wide-area networking, SASE helps protect OT endpoints in distributed environments.
The Future of OT Endpoint Security
As OT environments continue to evolve, the future of endpoint security will be shaped by advancements in technology and increased regulatory scrutiny. Key trends include:
- Integration of IT and OT Security: Unified security frameworks that address both IT and OT threats.
- Adoption of Blockchain: Blockchain technology for secure data exchange and device authentication.
- Increased Automation: Automated security tools for real-time threat detection and response.
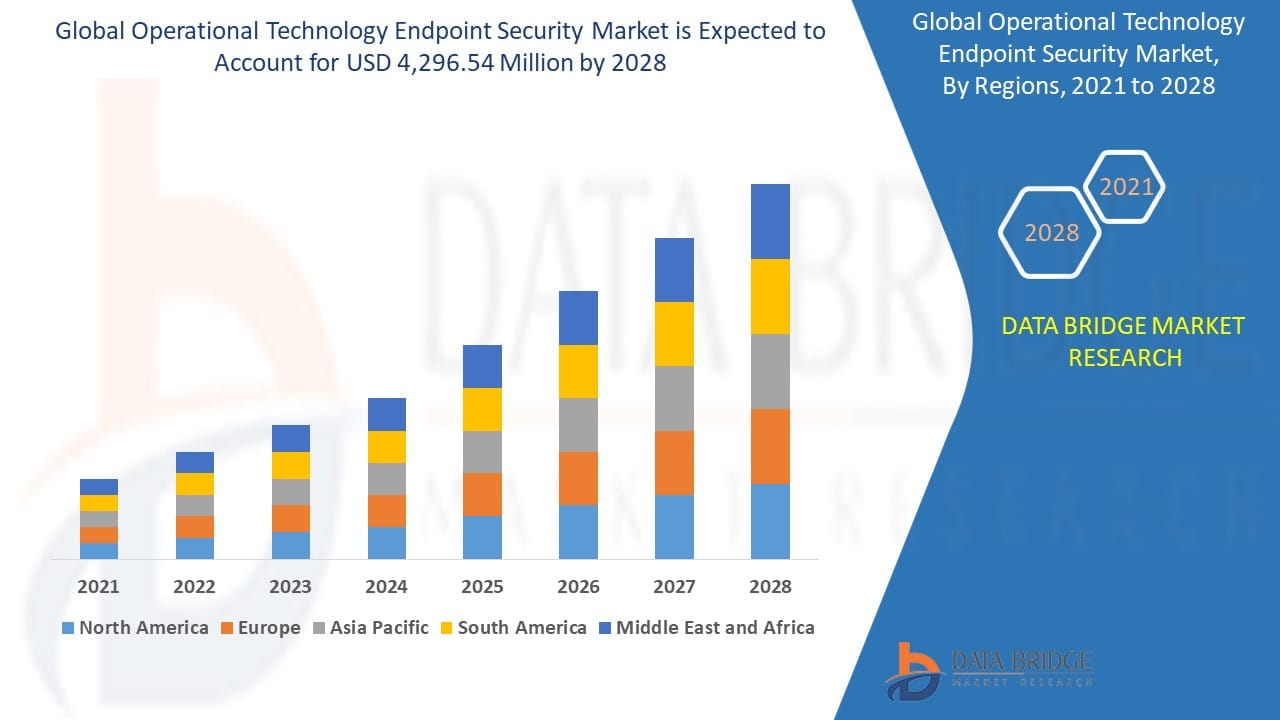
Growth Rate of Operational Technology Endpoint Security Market
The operational technology endpoint security market is expected to develop at a compound annual growth rate (CAGR) of 40.10% from 2021 to 2028, reaching an estimated value of USD 4,296.54 million. An important reason propelling the operational technology endpoint security market is the growing number of endpoints and Byods across companies.
Conclusion
Understanding and implementing OT endpoint security is no longer optional but essential for safeguarding critical infrastructure. By addressing unique challenges, leveraging emerging technologies, and adhering to best practices, organizations can build a robust defense against evolving cyber threats. In doing so, they ensure not only operational continuity but also the safety and resilience of their systems in an increasingly connected world.